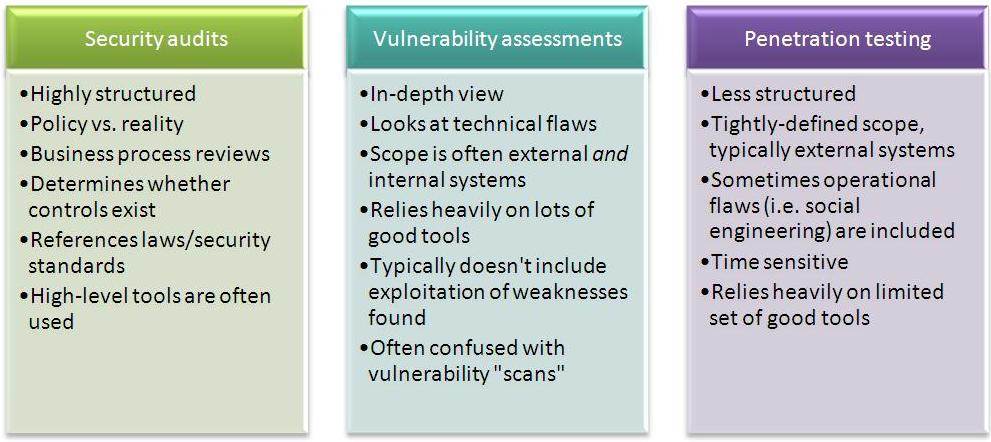
Cybersecurity AssessmentPosted by Adell on December 17th, 2020 What Is A Vulnerability AssessmentAlso, costs usually are specified in tactical terms like shed profits, public relations initiatives required to recover brand name picture, and preventing lawsuits. When the prospective losses are recognized for different kinds of assault they can be managed like any other regular company decision concerning threat. In practice, this ends up being a two-way conversation in between the tactical professionals as well as the exec planner to make great choices together utilizing the threat analysis as an usual point of recommendation. A danger assessment is the only tool that is totally suited for tactical discussion and choice making. Lining up tactical remedies like susceptability evaluations and penetration examinations to match the high-level locations of risk as established by a threat evaluation is a basic, effective method to make certain the ideal quantity of cash as well as initiative is being invested in the right areas. There are several kinds of protection analyses within info protection, and also they're not always easy to keep separately in our minds (particularly for sales kinds). A susceptability evaluation is a technological evaluation developed to produce as lots of susceptabilities as possible in an environment, together with extent and remediation top priority details. This is mostly because sales individuals assume the last sounds cooler, bless their hearts. The susceptability assessment is best utilized when protection maturation is low to tool, when you need a prioritized list of whatever that's incorrect, where the goal is to fix as numerous points as feasible as successfully as possible. A Penetration Test is a technical evaluation designed to accomplish a certain objective. Next Level Security Threat Assessments And Cyber SecurityThe Penetration Examination is frequently confused (and/or conflated) with the vulnerability evaluation. Another method to assume regarding this is to imagine susceptability assessments as searching for safety issues when you know/assume they exist, and infiltration screening as confirming a setup when you think it to be protected. Carrying Out an Infiltration Test against a reduced or moderate safety and security store will simply generate recommendation all-time-greats like, "Execute patching across the organization", "Disable non-active customers", and " Understand where your sensitive data is". Do not waste money on a Penetration Examination unless you have actually already undertaken one or seventeen susceptability assessments and after that remediated every little thing that was discovered. A Red Team "analysis" is something of a misnomer in the company context because company Red Group solutions need to ideally be continuous as opposed to point-in-time. So it needs to ideally be more of a service than an assessment. But despite that distinction, the central objective of a business Red Team is to improve the top quality of the company details protection defenses, which, if one exists, would be the business's Blue Group. In the instance of corporate Red Teams, the org they're improving is heaven Team. Red Group services should, in my viewpoint, always have the following 5 aspects: Business Independece, Defensive Sychronisation, Continual Operation, Opponent Emulation, and Effectiveness Measurement. Red Group services are most typically confused with Infiltration Testing. Cybersecurity & Risk AssessmentsPeople confusing the 2 are primarily seeing "Red Teaming" as a sexier, more exclusive sort of Infiltration Test. They are not the same. An Infiltration Test is a specified, scoped, as well as point-in-time evaluation that has particular goals for success or failure. A business Red Group (whether interior or outside) is a constant solution that imitates real-world assaulters for the purpose of boosting the Blue Group. [youtube https://www.youtube.com/watch?v=2VGOz5knADk] Red Team solutions are best used when an organization has covered the fundamentals of solid vulnerability administration and contends least some ability to identify as well as reply to harmful or dubious actions in the atmosphere. If a company is still having a hard time with standard possession management, patching, egress traffic control, and also other fundamentals, it's generally ideal that they obtain those addressed before hiring or constructing a "Red Team". If you do not have a Blue Group, you probably do not need a Red Team: An audit can be technical https://renitconsulting.com/contacts/ and/or documentation-based, and concentrates on how an existing setup contrasts to a preferred criterion. This is an important point. It does not show or confirm safety and security; it confirms uniformity with a provided point of view on what security suggests. Audits are usually puzzled with rather much any kind of various other type of security evaluation where the goal is to find vulnerabilities as well as repair them. That can be part of an audit, if there's a product in the requirement that claims you shouldn't have susceptabilities, but the essential feature is mapping current state versus an arbitrary requirement. 3 Types Of Cybersecurity AssessmentsSignificantly, compliance ought to not be used to show protection. Secure companies are considerably more probable to be certified (if examined), but compliant companies must lay no claims to being safe and secure even if they are in conformity with common X or Y: The white/grey/black analysis parlance is made use of to indicate just how much inner details a tester will be familiar with or use throughout an offered technical assessment. A grey-box analysis is the following degree of opacity down from white, suggesting that the tester has some information but not all. The quantity varies. A black-box assessment as you're with any luck guessing is an assessment where the tester has no inner understanding concerning the atmosphere, i. e. it's performed from the opponent perspective. They're most typically coupled with susceptability assessments where you're trying to locate the most problems feasible, and also that offers significant incentive to open up the curtains a little bit. Keep in mind that the objective of a vulnerability evaluation is to discover as lots of issues as possible, so hiding internal information from a tester that maintains them from finding problems doesn't harmed them,it hurts you. Like it? Share it!More by this author |