Little Known Facts About Cyber Security Ot.Posted by Trapani on March 18th, 2021 Facts About Scada Ot Cybersecurity UncoveredTable of ContentsThe 8-Minute Rule for Operational Technology Cyber SecurityNot known Details About Ot Cyber Security A Biased View of Cyber Security OtHow Scada Ot Ics Cybersecurity can Save You Time, Stress, and Money.Cyber Security Ot for DummiesThe Best Guide To Scada Ot CybersecurityGet This Report about Scada Ot Ics Cybersecurity Depending on to the 2019 Ponemon Cyber Surveillance in Operational Modern Technology Report, over 60% of participants discuss issue concerning an assault versus functional innovation (OT). But what is OT? When it pertains to bodily units, OT may be specified as a network-connected gadget that observes or handles methods, and occasions beyond Infotech (IT). Cybersecurity describes technological and management methods that protect devices coming from strike. Along with OT cybersecurity, these processes include the discovery, tracking, as well as remediation of network-connected OT devices had an effect on through unusual habits. The boost of OT devices used in markets including health care and lifestyle scientific researches has actually created OT cybersecurity more vital. Not known Facts About Ot Cyber SecurityAnd also uses of OT in wise properties that utilize wireless units to check and manage bodies such as heating, venting, and a/c (HEATING AND COOLING) count on sturdy OT cybersecurity. In comparison to OT cybersecurity, IT teams focus much less on tool resilience and also even more on the integrity of details. Thereby, IT teams as well as OT groups might possess different top priorities. The problem along with OT cybersecurity is actually that many equipments are operating obsolete software application, or even they might do not have after-market surveillance patches. This offers hackers an even greater possibility to endanger them or even corrupt all of them with malware as well as interrupt operations. Windows susceptibilities like BlueKeep and DejaBlue remain to be discovered in outdated Microsoft window bodies. Cysol Networks. How Cybersecurity Ot can Save You Time, Stress, and Money.Depending on to the 2020 International Risk File by OT security firm CyberX, in need of support and unpatched system software including Windows XP, Windows 2000, and also currently Microsoft it and ot window 7 represent 71% of networks they examined. When an OT cybersecurity event develops, the security team might have little bit of to no context concerning the tool. But unit manager, place, consumption, software program variation and also latest maintenance file could be overlooking. When this happens, there's a risk that the incorrect remediation steps are taken, like separating a clinical device. In a field like healthcare, it is actually vital that an accredited clinical developer is actually dispatched to remediate the gadget. The Single Strategy To Use For Ot Cyber Security MeaningTo deal with these OT cybersecurity obstacles, what is actually required is the ability to track as well as preserve a correct stock of OT assets as well as the information about them. When a device is actually obtained as well as provisioned, the gadget professional or a third party area specialist have to have the ability to input the unit information into the stock when they function in-person or from another location on the device. This gadget stock works as the solitary resource of fact that obtains an update when regimen upkeep happens, where employees will certainly enrich the tool data along with any kind of brand new information. But past gadget invention and also developed tool data, there need to be protection musical arrangement, hands free operation, and also feedback method and also device of report where the inventory and safety and security occasions records can easily be ingested (Cysol Networks). The 5-Minute Rule for Ot CyberWhen a protection celebration takes location, the surveillance team can easily see the full circumstance of the gadget. They'll know that the tool owner is actually as well as what removal procedure should be complied with therefore a work purchase could be sent off to the device engineer, or even suppliers or service suppliers industry professional. And also the work purchase method may be tracked in order that surveillance, IT, and also the device engineers are actually maintained knowledgeable of the remediation status. That's because Nuvolo ends up being the system of report. Nuvolo will certainly consume safety info, compare the gadget's IP as well as MAC COMPUTER handle, and also fully contextualize it with factors like the unit usage, what PHI records the tool is actually saving or even accessing, and also unit maintenance reports. Nuvolo's OT Security system, when integrated along with real-time monitoring units offers the security and company administration groups discussed exposure into gadget position. A Biased View of Ot Cyber
In lead-in the field's initial OT cybersecurity option built on ServiceNow, Nuvolo assists customers attain better item, location, and patient protection while safeguarding important commercial infrastructure. You can watch a complete demonstration on just how OT Cyber can assist you manage your non IT hooked up units by contacting us below https://www. nuvolo.com/product-walkthrough/. It is actually along with developing concern that cyberpunks are considerably targeting ), important for availability, production and protection of. Strikes against OT have actually ballooned in the final couple of years. Electricity companies help make up a majority of these assaults a spike steered by aging assets, out-of-date safety strategies as well as increased connection. The Only Guide to Cyber Security Operational TechnologyThis research covers subjects including: The new danger outpost in the electricity market and what the sector must do to prep. The relationship between connection, openness as well as knowledge. Why safety and security analytics are actually an essential part of any company. Gartner determines OT security as, "Practices and modern technologies used to (a) secure folks, resources, and details, (b) monitor and/or control bodily devices, procedures as well as celebrations, as well as (c) initiate condition modifications to company OT bodies." OT protection remedies include a vast variation of security technologies coming from next-generation firewall programs (NGFWs) to security relevant information and also activity administration (SIEM) bodies to identification gain access to and also control, and also far more - Cysol Networks. Like it? Share it!More by this author |


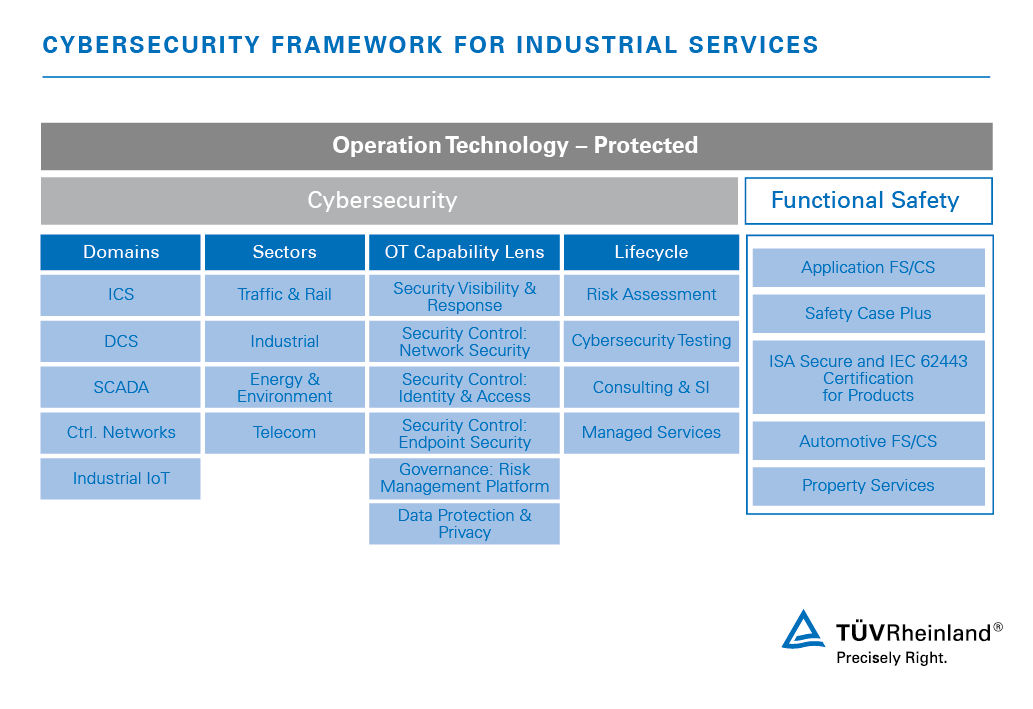 All about Scada Ot Cybersecurity
All about Scada Ot Cybersecurity