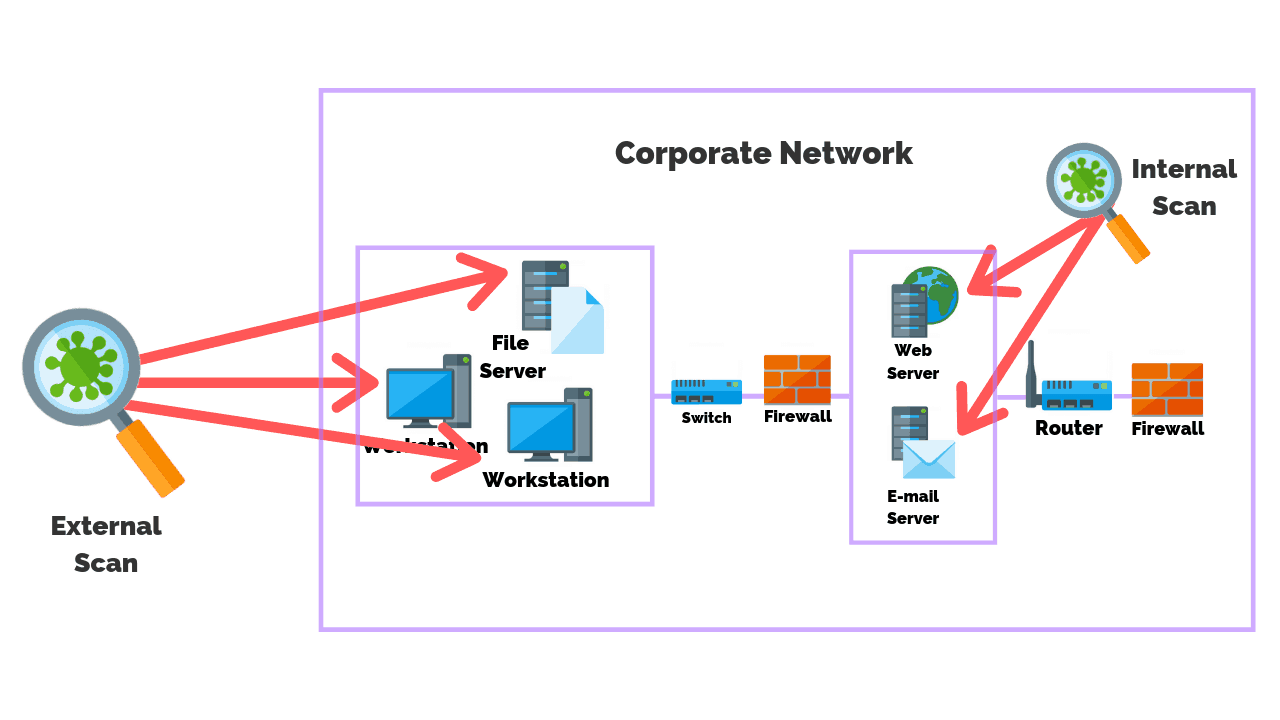
Vulnerability Scanning: What It Is And How To Do It RightPosted by Adell on April 29th, 2021 Vulnerability Scanning ToolsHackers can swiftly make use of these spaces. Vulnerability scanners commonly generate a lengthy checklist of danger variables, and also admins are seldom able to resolve all identified threats quickly as well as effectivelyit just requires way too many sources to examine and address each and every single product. Several automated devices provide positions of risks, from high to low, computed using factors like how much time the threat has actually been in the system and whether the effect to the system would be major or small. Admins need to initially recognize one of the most essential susceptabilities and also focus on those items. For each and every thing, think about: if a poor star manipulated this security void, what would certainly the impact be? Is delicate information at threat? Does this safety hole open a huge part of the network to hackers or a limited section? You additionally intend to take into consideration the chance of a criminal exploiting a safety and security void: while internal network and physical access are susceptible to staff member actions, outside network openings leave your business data open to the globe, which is substantially more hazardous. The purpose of reviewing safety and security gaps is to prioritize the susceptabilities needing immediate interest. Few IT groups have limitless time and also sources for attending to each and every single item that crosses their paths. In truth, you'll need to concentrate on the big-ticket items first, ideally with computerized help with your protection software program. Additionally, it overlaps with other vulnerability management techniques that can give crucial network understandings: Likewise called pen screening, this method is essentially about hacking your very own system before another person can. You're fairly analyzing your very own assault surface (or working with someone else to do so) via attempting to barge in and also "swipe" data. Network Vulnerability Scanning And Why You Need It NowThis resembles pen testing but is recurring, automated, as well as quantifiable. Basically, it allows you to guarantee your protection steps are efficient by subjecting them to routine testing as well as validation. Tools that undertake violation and strike simulation are more recent to the market and work in a different way from vulnerability scanner tools for one, they're handled by outdoors groups, so you have to make sure you rely on the vendor. Anti-virus software application is preferred, but it takes a limited technique to shield your network. It's concentrated on capturing and also getting rid of malware within the network, while ideally avoiding it from going into the network in the initial place. These antivirus devices have much less to do with taking care of network safety spaces than with attending to particular risks, like ransomware, spyware, Trojans, and the like. Web application scanning tools try to find susceptabilities within internet applications, either by imitating attacks or by assessing back-end code. They can capture cross-site scripting, SQL shot, path http://mspchj874.image-perth.org/there-s-been-a-huge-spike-in-online-shopping traversal, unconfident setups, as well as a lot more. These devices work on a similar principle as susceptability scanners. Although many admins are concerned with zero-day assaults, evidence to suggests misconfigurations as well as missing spots are the major powerlessness for harmful hacks. Scanning for and also fixing these errors aids make sure consistency across your systems, even when properties transform. These measures can also be critical for conformity. Admins intending their vulnerability scanning strategy have numerous approaches at their disposal. In truth, you might want to try a selection of check types as component of your overall safety and security administration, as testing your system from different angles can assist you cover all the bases. Best Network Vulnerability Scanning SoftwareWith an inner network scan, you'll wish to run threat discovery on the regional intranet, which will assist you understand security openings from the within. Likewise, admins ought to examine their network as a logged-in customer to establish which vulnerabilities would be easily accessible to relied on customers or customers who have accessed to the network. Likewise, it's crucial to scan the network as a trespasser might, to recognize what data might fall right into the hands of those without trusted network accessibility. A comprehensive check make up nearly every kind of device managed on the network, including web servers, desktop computers, digital makers, laptop computers, mobile phones, printers, containers, firewalls, and switches over.
In addition, the check may recognize unauthorized tools. Preferably, with a detailed check, no dangers go neglected. Nevertheless, these scans can utilize up bandwidth as well as might be impractical to run usually. Restricted scans concentrate on certain gadgets, like workstations or software program, to expose an extra details protection photo. With so numerous possible risks standing out up on networks and web applications, finding vulnerabilities is a vital task for IT admins. Whatever sort of network susceptability scanner you select, search for a device that accomplishes some or all of the adhering to functions, depending upon your demands: The first action of susceptability scanning is to find system weaknesses throughout the network. This can mean using a tool to try to catch and also also exploit safety spaces as it scans the attack surface. What Is Vulnerability Scanning?Some vulnerability detection tools are extra targeted as well as work to determine missing software application spots or firmware updates. The second step is to categorize vulnerabilities, to prioritize action items for admins. Susceptabilities can include packet abnormalities, missing out on updates, script errors, as well as a lot more, as well as threats are generally focused on by a combination old as well as determined threat degree. Not all security tools both determine concerns as well as give admins a means to automatically resolve them. Some VM tools are focused on keeping an eye on solely, leaving it approximately admins to take the following action. Yet some are constructed to deal with tool concerns, like arrangement mistakes, possibly getting to many gadgets at the same time to conserve admins hours of job. If you're looking to make a concrete change to your network to assist protect against safety and security violations, I recommend SolarWinds Network Configuration Supervisor (NCM). While not what some may identify as a standard "scanner" tool, NCM does a wonderful work in instantly identifying setup issues throughout multi-vendor network gadgets as well as can promptly deploy firmware repairs to loads or thousands of tools at the same time. Like it? Share it!More by this author |