Protection Against Internal And External Threats Under FirewallPosted by Levi Breretonl on August 25th, 2016 The security of a database is as important as the execution of the files. A safe record keeping is assured to limit the access to personal and commercial sensitive files. Firewall as the first line of defence against both internal and external threats. Many web application firewalls are active now-a-days, which provide a high performing line of defence for all kinds of files. The firewall acts as a barrier against harmful incoming and outgoing traffics. This network security system monitors and controls the harmful traffics. It establishes a boundary between trusted & secure internal networks and outside networks. The firewalls are categorised as network firewalls and host-based firewalls. Network firewalls are a software appliance, which run on a general purpose hardware. Host-based firewalls provide a barrier of software on the host network and the traffic going in and out of that single network.
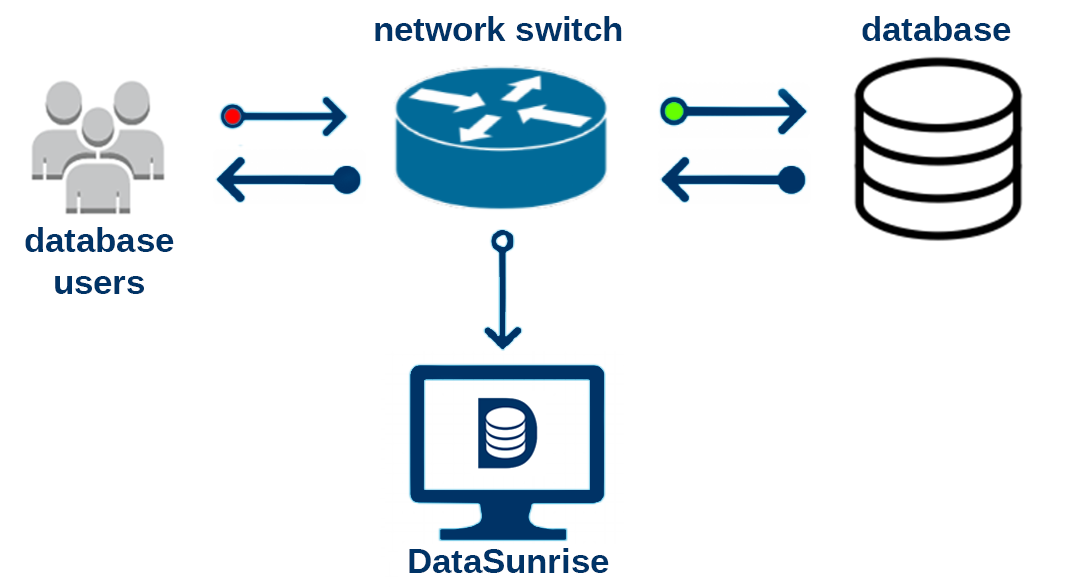
A trustworthy and reliable firewall Database firewall is a type of web application firewall, which monitors databases to identify and protect against specific attacks. These external attacks are on the sensitive information stored in the databases. It also enables and audits all the accesses to the database system through the logs. This firewall is generally deployed in-line with database server. Some of the database servers also monitor the local database events. Under this firewall both the hardware and software agents are deployed to work simultaneously. This firewall includes a set of pre-defined and customised security audit policies. The attacks are identified on past threats. SQL statements are compared to the past signatures. The statements are updated frequently by the vendors. All the attacks are not similar. So, great arrangements are done to protect against unfamiliar threats also. A fine line is drawn between white list and black list of certain harmful commands. Some of the practices done under database security are following:- ● Deletion of unused accounts Like it? Share it!More by this author |