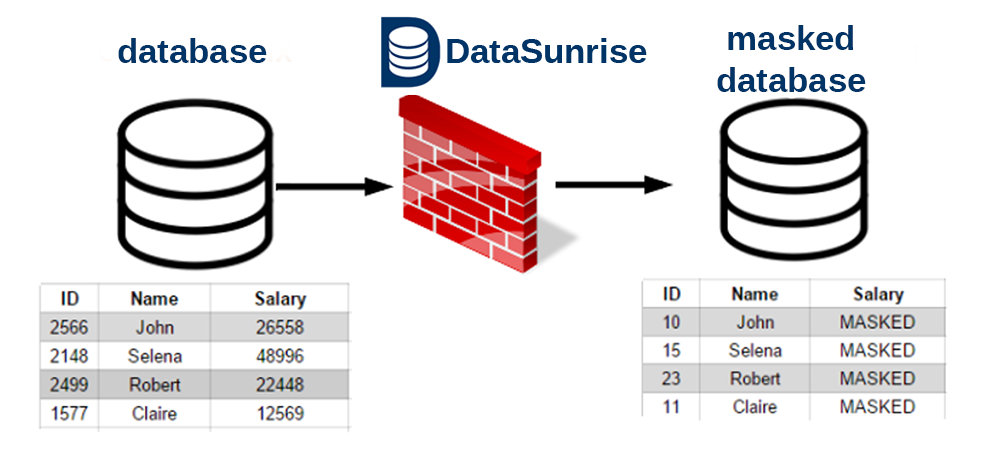
Get Great Help From An Effective Database Security Suit!Posted by Levi Breretonl on December 22nd, 2016 Nowadays, there are a number of organizations making use of Greenplum database in terms of storing their important and sensitive data. If you are also using the same database to store your important data or information then you should also consider putting its security on primary basis. This particular database has been mainly developed for database warehouse. Moreover, it is developed primarily for analytical processing of big data. Though, it is an efficient database but you should consider the importance of its security above all. By using a security suit, you would surely be able to get the best possible Greenplum security. An effective security tool can efficiently analyze all the traffic generated by several database functions. Such tools can easily provide great help when it comes to getting full protection from hacker attacks to the corporate data. The other benefit of security tools is that it protects database from unauthorized access to the database resources.
There are actually a number of benefits of using a security tool for the purpose of security of any specific database. Such tools not only protects database from hackers or outsiders but also it protects database from the inner threats. For instance, there could easily be seen many cases of data leaks by the company employees. Therefore, it is really very important for companies to take help of a security suit in order to keep their data safe from both outsiders and insiders. By using an effective enterprise database monitoring and protection tool, one can be easily sure for getting 24/7 database security. Such tools also maintain complete control over the sensitive data on premises as well as in the cloud. As a result, an organization can easily be sure for getting the ultimate level of security for their specific database. Moreover, it can be sure for staying agreeable with the authoritarian requirements. A security tool can easily monitor user activity. Such tools are well known in terms of detecting prohibited and unusual activity of the database users. More to the point, Greenplum security tool also captures database activity as well as user behavior accurately by detailed logging. Besides all this, log information is used for the purpose of continuous controlling of activities and prevention of data leaks, attempts of access rights abuse as well as hackers attacks. So, what are you waiting for? Make selection of the right security tool for your specific database! Related Article :- Are You Using Greenplum Database? Like it? Share it!More by this author |